Malicious hackers employ distributed denial of service (DDoS) attacks to disrupt business by preventing legitimate users from accessing organizations’ websites. In 2018, the direct and indirect losses caused by a single DDoS attack ranged from US$120,000 to US$2 million. Between 2016 and 2017, the number of DDoS attacks increased by 29 percent, and in 2017, the average attack size was 26 gigabytes per second.1 In most cases, hackers use an army of botnets to carry out the DDoS attack, making it difficult to detect the hacker and prevent future attacks.
DDoS attacks vary in severity across different industries and networks. As a result of DDoS attacks, industries which rely heavily on the real-time health of their networks such as gaming, video streaming, banking, financial services and insurance, lost US$4 million in 2015.2 Since then, losses have only increased. In 2019, an unnamed streaming application enterprise was the target of a two-week-long DDoS attack that peaked at 292,000 requests per second, originating from 402,000 different Internet Protocol (IP) addresses.3 The enterprise lost approximately US$200 million, with a peak loss of US$500,000 per hour.4 In 2016, many large digital organizations, including Netflix, Spotify, Twitter, BBC, CNN, The New York Times and other entertainment services such as HBO Now and Elder Scrolls, were offline because of the infamous Dyn server attack.5
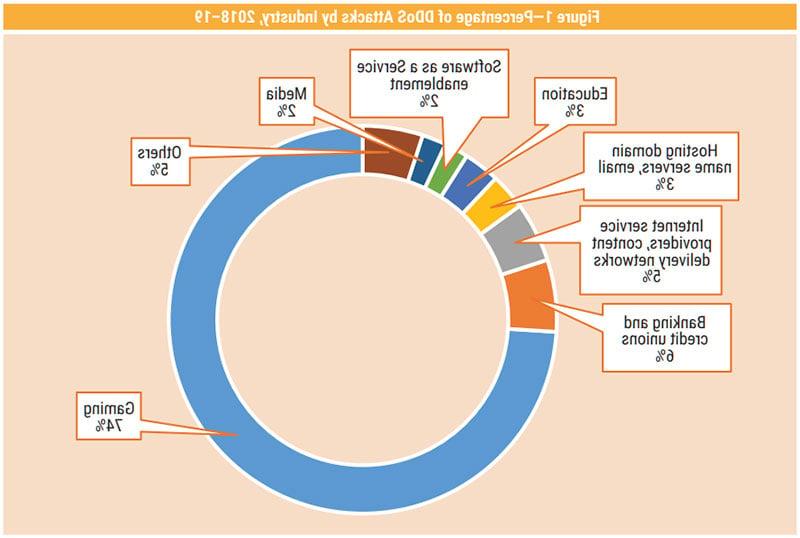
The entertainment industry (e.g., video streaming, music streaming, gaming) has been hit hard by DDoS attacks. Figure 1 shows that in 2018-19, the gaming industry accounted for 74 percent of the DDoS attacks recorded by Akamai’s Prolexic platform.6 Gamers are a tight-knit network, and they constitute a high-spending niche segment.7 Hackers can attack multiple nodes by infecting a compromised network of gamers and spreading the DDoS botnets to other user nodes. Many hackers target popular games to get access to accounts while they are being used in real time. Hackers can hide their trails by passing themselves off as gamers and exchanging their stolen money for in-game items or currency.8
Enterprises lose approximately US$50,000 per hour when under a DDoS attack.9 Thus, it is important to quantify the probability of detecting a DDoS attack and the losses associated with it.
Proposed Model
Figure 2 illustrates a risk assessment and mitigation model for DDoS attacks in the gaming industry. The following issues are explored:
- What is the probability (p) of detecting a DDoS attack using the model?
- What is the expected loss (E[L]) for the enterprise if the model fails to detect the attack vector?
- How can risk and losses be reduced?

The following steps are proposed for risk assessment and mitigation:
- Compute the risk of not detecting a DDoS attack by analyzing a past attack data set.
- Compute the severity of a DDoS attack that has not been detected by the model.
- Generate a risk and severity heat matrix for all DDoS attacks that have not been detected.
- If risk and severity are both high, then resort to reduction and transfer of risk to cyberinsurer, otherwise only transfer risk to cyberinsurer.
Data
Figure 3 describes the data set used to test the proposed model. It consists of 10,329 records of seven DDoS attack types grouped into five overlapping attack classes in the gaming industry for the years 2012 to 2018.10, 11, 12

Each record has the following attributes: start timestamp, end timestamp, bits per second (bps), packets per second (pps) and class of attack detected. The bps and pps attributes are highly correlated. Thus, the final attack feature vector consists of bps, duration, type, class and attack indicator variables. The data set has been divided into training (n=6,197) and testing (n=4,132) data sets in a ratio of 60:40.
Methodology
The Kernel-based Naïve Bayes (KNB) classifier has been used for classifying DDoS attacks into 5 attack classes (A, B, C, D and E), as the training data do not follow any parametric class distributions. Bayesian classifiers are statistical classifiers used to predict class membership probabilities (i.e., the probability that a given data set record belongs to a particular class). The class with the highest probability is the dominant class for the record.13 The Naïve Bayes classifier is more accurate if the attributes are inherently independent. Because this data set has attack-tuples, with two independent classes overlapping and forming a hybrid attack vector, the KNB classifier was chosen.
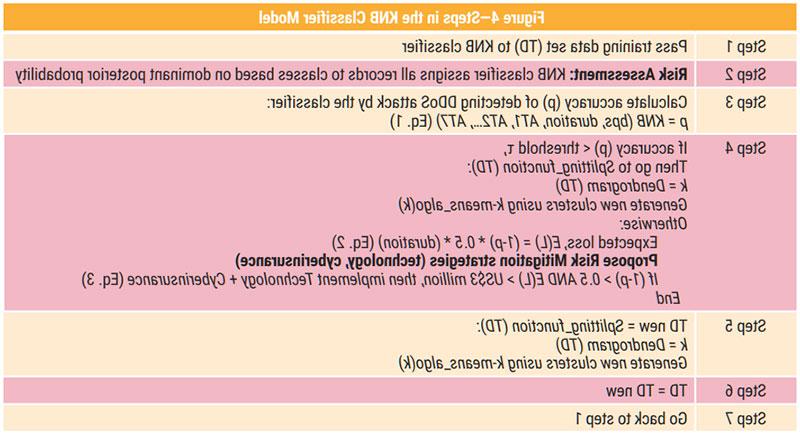
Figure 4 describes the steps followed by the proposed methodology to produce classification accuracy above a certain value τ (at least 70 percent).14 The threshold τ is based on the criticality of the online mode of operation vis-à-vis overall operations. The methodology then calculates the expected loss and suggests mitigation strategies to reduce losses.
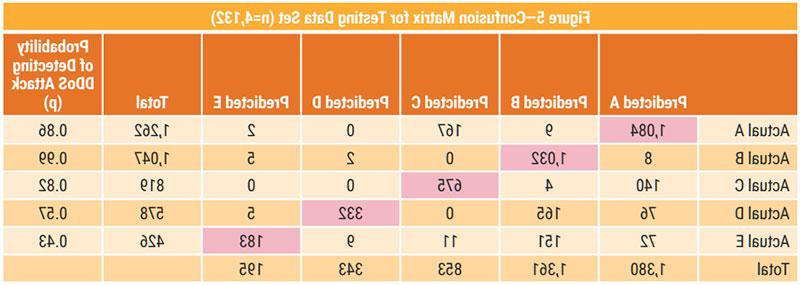
MATLAB 2019a software was used to analyze the data. Figure 5 shows the confusion matrix of the initial run. The diagonal (shaded) elements indicate the number of instances in which attacks were correctly classified (e.g., 1,084 for class A); in addition, 178 records were misclassified as false positive and 296 as false negative. The model correctly classified 99 percent of class B attacks and 43 percent of class E attacks.
Next, the data set for class E, with the highest number of misclassifications (57 percent), was visualized using hierarchal clustering (figure 6). This showed the presence of three distinct branches, based on the dissimilarity index. Therefore, original class E (n=1,008) was split into three subclasses—E1 (n=884), E2 (n=42) and E3 (n=82)—using a k-means clustering algorithm.

Results
The following sections discuss the results for computing the probability (p) of detecting a DDoS attack using the model, the E[L] for the enterprise if the model fails to detect the attack vector and risk mitigation strategies.
Probability of Detecting a DDoS Attack
Figure 7 shows that the overall accuracy of the
classifier was 80.39 percent. Diagonal elements
(shaded) represent instances in which the model
correctly classified attacks (3,322 out of 4,132
records). The model correctly classified 97 percent
of class B attacks and 100 percent of class E3
attacks.

Loss Computation After a DDoS Attack
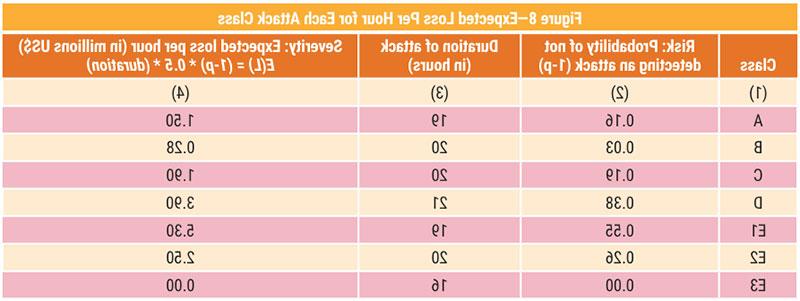
In Figure 8, column 2 demonstrates the risk (i.e.,
probability of not detecting an attack [1-p]), and column 4 illustrates the severity of DDoS attack
(i.e., of expected losses for each attack class
-based on Eq. 2).
Risk Mitigation Strategies
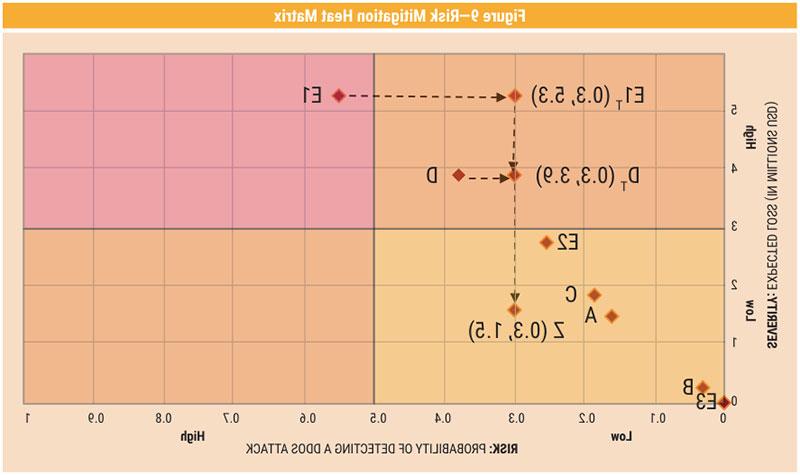
Figure 9 depicts a heat matrix calculated from the
model that situates the different DDoS attacks in
terms of Risk × Severity. This helps a chief
technology officer (CTO) to prioritize the risk
mitigation strategy, such as technological
intervention to reduce the risk or transfer risk
through cyberinsurance. For example, a DDoS
attack of class E1 is in the high risk, high severity quadrant, while classes A, B, C, E2 and E3 are in the
low risk, low severity quadrant. For example, the
CTO of an enterprise at risk of DDoS of class D and
class E1 attacks should consider implementing the
following risk mitigation strategies: First, add
stringent firewalls or intrusion detection systems or
divert excess or illegitimate traffic to backup
servers or content delivery networks (CDNs) to
reduce the risk and, thus, lower the severity of DDoS
attack. Next, transfer the residual risk by
subscribing to cyberinsurance policies, thus moving
into the low risk, low severity quadrant.15, 16, 17, 18
Conclusion
The previously described model helps to compute the risk (probability of not detecting a DDoS attack) and the severity (expected losses) by using past attack data. CTOs can use it to design their risk mitigation strategy in terms of technological intervention to reduce the risk and transfer risk through cyberinsurance. While this discussion focused on the gaming industry, the model can be replicated for any industry facing DDoS attacks so that risk assessment and mitigation strategies can be developed.
Endnotes
1 Abrams, L.; “Dramatic Increase of DDoS Attack
Sizes Attributed to IoT Devices,” Bleeping
Computer, 12 September 2018,
http://www.bleepingcomputer.com/news/security/dramatic-increase-of-ddos-attack-sizes-attributed-to-iot-devices/
2 Zumberge, M.; “Cyber Attacks on the Rise in
Media Biz Since Sony Hack: Survey (Exclusive),”
Variety, 5 November 2015, http://variety.com/2015/digital/news/sony-hack-anniversary-cybersecurity-data-1201633671/
3 Shani, T.; “Updated: This DDoS Attack
Unleashed the Most Packets per Second Ever.
Here’s Why That’s Important,” Imperva, 12 June
2019, http://www.imperva.com/blog/this-ddos-attack-unleashed-the-most-packets-per-second-ever-heres-why-thats-important/
4 Bezsonoff, N.; “The State of DDoS Attacks in
2017,” Neustar, 11 October 2017,
http://www.home.neustar/blog/neustar-global-attacks-and-cyber-security-insight-report
5 Chiel, E.; “Here Are the Sites You Can’t Access
Because Someone Took the Internet Down,”
Splinter News, 21 October 2016, http://splinternews.com/here-are-the-sites-you-cant-access-because-someone-took-1793863079
6 McKeay, M.; “Q4 2017 State of the Internet
Security Report,” Akamai, 28 December 2017,
http://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/q4-2017-state-of-the-internet-security-report.pdf
7 Ibid.
8 Ibid.
9 Op cit Bezsonoff
10 Op cit McKeay 2017
11 McKeay, M.; “2019 State of the
Internet/Security: Web Attacks and Gaming
Abuse,” Akamai, June 2019,
http://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/soti-security-web-attacks-and-gaming-abuse-report-2019.pdf
12 McKeay, M.; “2019 State of the
Internet/Security: DDoS and Application
Attacks,” Akamai, January 2019,
http://www.akamai.com/us/en/multimedia/documents/state-of-the-internet/state-of-the-internet-security-ddos-and-application-attacks-2019.pdf
13 Han, J.; M. Kamber; J. Pei; Data Mining:
Concepts and Techniques, Elsevier, The
Netherlands, 2012
14 Biswas, B.; S. Pal; A. Mukhopadhyay; “AVICSEco
Framework: An Approach to Attack
Prediction and Vulnerability Assessment in a
Cyber-Ecosystem,” AMCIS 2016: Surfing the IT
Innovation Wave—22nd Americas Conference on
Information Systems
15 Mukhopadhyay, A.; S. Chatterjee; K. K. Bagchi;
P. J. Kirs; G. K. Shukla; “Cyber Risk Assessment
and Mitigation (CRAM) Framework Using Logit
and Probit Models for Cyber Insurance,”
Information Systems Frontiers, vol. 21, iss. 5, p.
997–1018, 2017, http://doi.org/10.1007/s10796-017-9808-5
16 Das, S.; A. Mukhopadhyay; G. K. Shukla; “i-HOPE
Framework for Predicting Cyber Breaches: A
Logit Approach,” 46th Hawaii International
Conference on System Sciences, 2013,
http://doi.org/10.1109/hicss.2013.256
17 Biswas, B.; A. Mukhopadhyay; G. Dhillon;
“GARCH-Based Risk Assessment and Mean-Variance-Based Risk Mitigation Framework for
Software Vulnerabilities,” AMCIS 2017: A
Tradition of Innovation—23rd Americas
Conference on Information Systems
18 Biswas, B.; A. Mukhopadhyay; “Phishing
Detection and Loss Computation Hybrid Model:
A Machine-Learning Approach,” ISACA® Journal, vol. 1, 2017, http://wup.ozone-1.com/archives
Kalpit Sharma
Is a Ph.D. student in information technology and systems at the Indian Institute of Management (IIM) (Lucknow, India). His
research interests are privacy and risk issues in information systems, the economics of cybersecurity, healthcare IT, IT governance
and crowd-based digital business models. He can be reached at kalpit@iiml.ac.in.
Arunabha Mukhopadhyay
Is a professor of information technology and systems at the Indian Institute of Management. He is an ISACA Academic Advocate
for the IIM Lucknow ISACA Student Group. He is the recipient of the Best Teacher in Information Technology Management Award in
2011 by Star DNA-Group B-School Award, and he was also awarded the 19th Dewang Mehta Business School Award in 2013. He
can be reached at arunabha@iiml.ac.in.
