COBIT® 2019’s enterprise goal EG06 Business service continuity and availability must be foremost in everyone’s mind today due the ongoing pandemic situation. It is important to identify the critical components that need to be evaluated to assess the preparedness of an organization toward business service continuity and availability.
The COBIT® goals cascade (figure 1) provides a step-by-step approach for identification of the alignment goals and the governance and management objectives that are related to an enterprise goal. So, the first step is to find the alignment goals, followed by the related governance and management objectives.
Figure 1–COBIT 2019 Goals Cascade
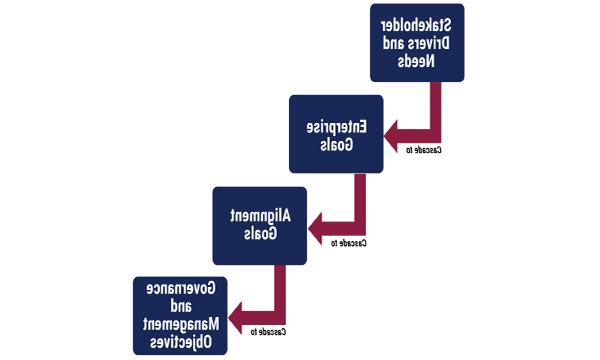
Source: ISACA®, COBIT® 2019 Framework: Introduction and Methodology, USA, 2018
The appendices in COBIT® 2019 Framework: Governance and Management Objectives provide several mapping tables, including the A.1.1 mapping table, which maps enterprise goals to alignment goals. Figure 2 maps enterprise goal EG06 with the alignment goals. The P in the Priority column indicates a primary priority and the S refers to secondary.
Figure 2–Mapping of Enterprise Goal EG06 With Alignment Goals
|
Alignment Goals |
Description |
Priority |
|
AG02 |
Managed I&T-related risk |
S |
|
AG05 |
Delivery of I&T services in line with business requirements |
S |
|
AG07 |
Security of information, processing infrastructure and applications, and privacy |
P |
The next mapping table to consult is A.1.2, which maps alignment goals with governance and management objectives. Figure 3 shows such a mapping of selected alignment goals with governance and management objectives. Only the objectives with a primary (P) priority are included.
Figure 3–Mapping of Selected Alignment Goals With Governance and Management Objectives
|
Governance and Management Objectives |
Description |
AG02 |
AG05 |
AG07 |
|
EDM03 |
Ensured risk optimization |
P |
|
P |
|
APO05 |
Managed portfolio |
|
P |
|
|
APO08 |
Managed relationships |
|
P |
|
|
APO09 |
Managed service agreements |
|
P |
|
|
APO10 |
Managed vendors |
|
P |
|
|
APO12 |
Managed risk |
P |
|
P |
|
APO13 |
Managed security |
|
|
P |
|
BAI02 |
Managed requirements definition |
|
P |
|
|
BAI03 |
Managed solutions identification and build |
|
P |
|
|
BAI04 |
Managed availability and capacity |
|
P |
|
|
BAI10 |
Managed configuration |
|
|
P |
|
DSS01 |
Managed operations |
|
P |
|
|
DSS02 |
Managed service requests and incidents |
|
P |
|
|
DSS03 |
Managed problems |
|
P |
|
|
DSS04 |
Managed continuity |
|
P |
P |
|
DSS05 |
Managed security services |
P |
|
P |
|
MEA01 |
Managed performance and conformance |
|
P |
|
For one enterprise goal (EG06), there are 3 alignment goals and 17 mapped governance and management objectives, even though the selection was restricted to only those objectives with a P priority. This is a large number of identified objectives and it may not be very practical to pursue each one of them. The initial focus could be on only those objectives that are directly mapped against alignment goal AG07. AG07 has a P ranking when mapped with enterprise goals. This results in a reduced list of objectives. Two more objectives may be included in this list due to their relevance to the current pandemic situation; although they are not classified as a P priority under AG07, they are listed under AG05: Align, Plan and Organize (APO) APO09 Managed service agreements and APO10 Managed vendors. Other objectives from the Deliver, Service and Support (DSS) group could be included at a later stage.
Figure 4 illustrates a shortlisted table of objectives.
Figure 4–Mapping of Shortlisted Governance and Management Objectives
|
Objectives |
Description |
AG02 |
AG05 |
AG07 |
|
EDM03 |
Ensured risk optimization |
P |
|
P |
|
APO09 |
Managed service agreements |
|
P |
|
|
APO10 |
Managed vendors |
|
P |
|
|
APO12 |
Managed risk |
P |
|
P |
|
APO13 |
Managed security |
|
|
P |
|
BAI10 |
Managed configuration |
|
|
P |
|
DSS04 |
Managed continuity |
|
|
P |
|
DSS05 |
Managed security services |
P |
|
P |
COBIT 2019 defines 7 components that are collectively responsible for achieving these objectives (figure 5). Failure of a single component could result in failure to achieve the objective; hence, the review process should include all the COBIT components of a governance system.
Figure 5–COBIT Components of a Governance System

Source: ISACA, COBIT 2019 Framework: Introduction and Methodology, USA, 2018
Among all the components, processes are the most elaborately documented. To review the processes, it is necessary to review all the underlying practices and activities. Figure 6 lists all the practices and number of activities relating to the selected objectives.
Figure 6–List of Objectives, Practices and Number of Activities
|
Objectives |
Description |
Practices |
Number of Activities |
|
EDM03 |
Ensured risk optimization |
EDM03.01 Evaluate risk management |
7 |
|
|
|
EDM03.02 Direct risk management |
5 |
|
|
|
EDM03.03 Monitor risk management |
4 |
|
APO09 |
Managed service agreements |
APO09.01 Identify I&T services |
6 |
|
|
|
APO09.02 Catalog I&T-enabled services |
3 |
|
|
|
APO09.03 Define and prepare service agreements |
5 |
|
|
|
APO09.04 Monitor and report service levels |
5 |
|
|
|
APO09.05 Review service agreements and contracts |
2 |
|
APO10 |
Managed vendors |
APO10.01 Identify and evaluate vendor relationships and contracts |
5 |
|
|
|
APO10.02 Select vendors |
7 |
|
|
|
APO10.03 Manage vendor relationships and contracts |
8 |
|
|
|
APO10.04 Manage vendor risk |
3 |
|
|
|
APO10.05 Monitor vendor performance and compliance |
6 |
|
APO12 |
Managed risk |
APO12.01 Collect data |
8 |
|
|
|
APO12.02 Analyze risk |
8 |
|
|
|
APO12.03 Maintain a risk profile |
7 |
|
|
|
APO12.04 Articulate risk |
5 |
|
|
|
APO12.05 Define a risk management action portfolio |
3 |
|
|
|
APO12.06 Respond to risk |
5 |
|
APO13 |
Managed security |
APO13.01 Establish and maintain an information security management system (ISMS) |
7 |
|
|
|
APO13.02 Define and manage an information security and privacy risk treatment plan |
7 |
|
|
|
APO13.03 Monitor and review the information security management system (ISMS) |
5 |
|
BAI10 |
Managed configuration |
BAI10.01 Establish and maintain a configuration model |
2 |
|
|
|
BAI10.02 Establish and maintain a configuration repository and baseline |
2 |
|
|
|
BAI10.03 Maintain and control configuration items |
4 |
|
|
|
BAI10.04 Produce status and configuration reports |
3 |
|
|
|
BAI10.05 Verify and review integrity of the configuration repository |
5 |
|
DSS04 |
Managed continuity |
DSS04.01 Define the business continuity policy, objectives and scope |
4 |
|
|
|
DSS04.02 Maintain business resilience |
8 |
|
|
|
DSS04.03 Develop and implement a business continuity response |
8 |
|
|
|
DSS04.04 Exercise, test and review the business continuity plan (BCP) and disaster response plan (DRP) |
6 |
|
|
|
DSS04.05 Review, maintain and improve the continuity plans |
4 |
|
|
|
DSS04.06 Conduct continuity plan training |
4 |
|
|
|
DSS04.07 Manage backup arrangements |
4 |
|
|
|
DSS04.08 Conduct post-resumption review |
3 |
|
DSS05 |
Managed security services |
DSS05.01 Protect against malicious software |
5 |
|
|
|
DSS05.02 Manage network and connectivity security |
9 |
|
|
|
DSS05.03 Manage endpoint security |
10 |
|
|
|
DSS05.04 Manage user identity and logical access |
8 |
|
|
|
DSS05.05 Manage physical access to I&T assets |
7 |
|
|
|
DSS05.06 Manage sensitive documents and output devices |
5 |
|
|
|
DSS05.07 Manage vulnerabilities and monitor the infrastructure for security-related events |
5 |
|
TOTAL |
8 |
42 |
227 |
As per this selection, 8 governance and management objectives, 42 practices, and 227 activities need to be reviewed. Looking at the volume of work, further prioritization can be done. It may be desirable to focus initially only on APO09 Managed service agreements, APO10 Managed vendors, DSS04 Managed continuity and DSS05 Managed security services. This reduces the work to review of 4 management objectives, 25 practices and 140 activities. The selection of actual number of objectives for review is left to the reviewer. Additional objectives for review could be selected depending on the availability of time and the relative importance of the objective as decided by the reviewer.
COBIT is an umbrella framework of good practices for achieving governance and management objectives. This is the reason a large list of items comes up for review. It is important to exercise judgment to identify and prioritize the work to be done and not follow these lists in a mechanical manner.
Components Under Review
Selection of the right processes, practices and activities is necessary but not sufficient to achieve the governance and management objectives since “Processes, practices, activities” is just one of the 7 components essential for the purposes described here. Inadequacy in implementing any 1 of the 7 components can lead to an inability to achieve the objective. In COBIT® 5, these were named “enablers;” in COBIT 2019, they are called “components,” thus highlighting their importance, as shown in this list:
- Processes, practices, activities–An effort has been made to reduce the number of processes, practices and activities to be reviewed to a smaller list. However, more objectives should be added to this list based on internal discussions and the availability of resources. Ideally, all the objectives mentioned in figure 6 should be covered. For each process under review, the key metrics achieved for the practices and the capability levels achieved and maintained for various activities should be ascertained and reviewed for adequacy.
- Organizational structure–For each practice listed in figure 7, determine if the responsibility and accountability have been properly identified and are being maintained.
Figure 7–Prioritized List of Objectives, Practices and Number of Activities
|
Objectives |
Objective Description/Processes Description |
Number of Practices |
Number of Activities |
|
APO09 |
Managed service agreements |
5 |
21 |
|
APO10 |
Managed vendors |
5 |
29 |
|
DSS04 |
Managed continuity |
8 |
41 |
|
DSS05 |
Managed security services |
7 |
49 |
|
4 |
4 |
25 |
140 |
- Information flows and items–The quality of information items, both for inputs and the resultant outputs, should be checked for each practice. There are 3 main criteria and 15 sub-criteria that define information quality, such as objective, relevant and current.
- People, skills and competencies–It is important to check whether the people involved in handling the practices and activities have appropriate skills and competencies and identify gaps, if any.
- Policies and procedures–The policies and procedures pertaining to various practices and activities should be reviewed.
- Culture, ethics and behavior–These intangible components must be checked against stakeholders’ expectations.
- Services, infrastructure and application–These must be adequate if successful implementation and execution of various practices and activities are to take place.
The final step in the evaluation of business service continuity and availability is summing up the findings, including documenting achievement of key metrics for the alignment goals and enterprise goal EG06. Failure in achieving any metrics will be traceable to a specific component.
This review process will identify gaps, if any, and provide direction for further improvements in the business service continuity and availability preparedness of the organization.
Avinash W. Kadam, CISA, CRISC, CISM, CGEIT, CISSP, CSSLP, GCIH, GSEC
Is a freelance cybersecurity mentor currently engaged in training and mentoring aspiring cybersecurity professionals and those who are new to this field. He worked for ISACA® as an advisor to the ISACA India Task Force for more than 3 years. Prior to this, he was involved in information security training and consulting for more than a decade. His career spans almost 5 decades of IT maintenance, operations, management, consulting and training. He coauthored Securing Sensitive Personal Data and Information Under India’s IT Act Using COBIT® 5 and RBI Guidelines Mapping With COBIT®5, both of which are available for download from ISACA. He is an accredited trainer for COBIT 2019.
